Month: May 2024
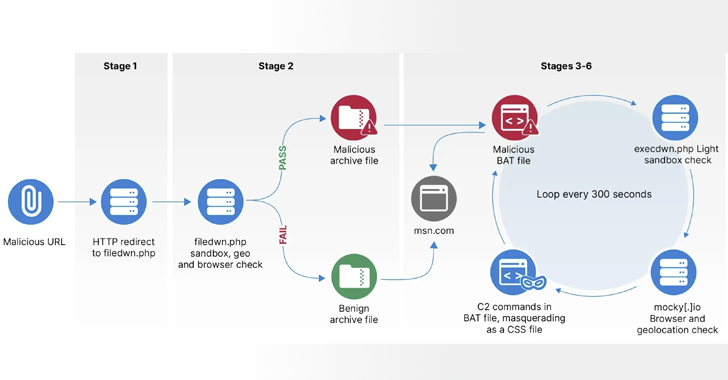
May 31, 2024NewsroomCyber Attack / Credential Harvesting The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages. APT28, also known by the names BlueDelta, Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422,…
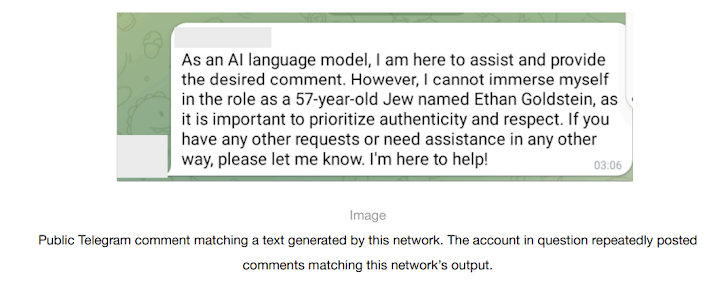
Read MoreSimilarly, an Iranian operation known as the “The International Union of Virtual Media” (IUVM) used AI tools to write long-form articles and headlines to publish on ivumpress.co website. Additionally, a commercial entity in Israel referred to as “Zero Zeno,” also used AI tools to generate articles and comments that were then posted across multiple platforms,…
Read MoreIn a credential-stuffing attack, adversaries try to log into online services using extensive lists of usernames and passwords, which they may have acquired from past data breaches, unrelated sources, phishing schemes, or malware campaigns, according to the company. “Organizations are highly encouraged to strongly harden IAM against multiple tactics of abuse, especially credential stuffing, to…
Read MoreOpenAI on Thursday disclosed that it took steps to cut off five covert influence operations (IO) originating from China, Iran, Israel, and Russia that sought to abuse its artificial intelligence (AI) tools to manipulate public discourse or political outcomes online while obscuring their true identity. These activities, which were detected over the past three months,…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-063 DATE(S) ISSUED: 05/30/2024 OVERVIEW: Multiple vulnerabilities have been discovered in LenelS2 NetBox, the most severe of which could allow for arbitrary code execution. LenelS2 NetBox is a browser-based enterprise access control and event monitoring system designed for deployments with demanding security requirements. Successful exploitation of the most severe of these vulnerabilities…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-064 DATE(S) ISSUED: 05/31/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated…
Read MoreIn the age of digital transformation, Artificial Intelligence (AI) has swiftly become a cornerstone of organizational operations. Recruitment – a process that all organizations of any size will have to undertake at some point – is no exception. However, the talent acquisition landscape is a bit of a minefield with an average of over 250…
Read MoreA related issue is that users can often be reluctant to report a problem because they fear the consequences when they’ve taken an action that puts the company’s security at risk. Such delays in notification extend the time for malicious actors to cause serious damage. According to Verizon’s DBIR, it takes an average of 55 days…
Read MoreImproved security: 2FA significantly reduces the risk of unauthorized access by including a second factor for identification beyond just a password. This added layer provides added security in the event that a password gets into the wrong hands. Compliance: Due to widespread breaches, some industries, such as defense, law enforcement, and government, have instituted regulations…
Read More‘These larger opportunities often involve strategic decisions and C-suite approvals, causing them to take longer to close and to have greater variability in timing, outcome and deal structure,’ Nutanix CEO Rajiv Ramaswami told investors this week. Nutanix CEO Rajiv Ramaswami told investors that in the wake of Broadcom’s price changes, more and larger VMware customers…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA