The murky world of password leaks – and how to check if you’ve been hit
by nlqip

How To
Password leaks are increasingly common and figuring out whether the keys to your own kingdom have been exposed might be tricky – unless you know where to look
03 Jun 2024
•
,
6 min. read

Recently, I came across a report detailing “the mother of all breaches” – or to be more exact, the leak of a vast compilation of data that was stolen during a number of attacks on various companies and online services, including LinkedIn and Twitter (now X). The data cache reportedly comprised an astonishing 26 billion records that were replete with a range of sensitive information, including government data and people’s login credentials.
While this is not the first time that a massive stash of user data has been there for the taking, the sheer number of compromised records eclipsed previous known leaks (and their compilations). Just consider that the infamous Cam4 data leak in 2020 exposed close to 11 billion records of various kind and the breach at Yahoo in 2013 compromised all three billion user accounts. Lest we forget: the aptly named Collection No. 1, which made it onto the open internet in 2019, exposed 773 million login names and passwords previously stolen from various organizations, before being followed by four more “collections” of this kind just weeks later.
Where does that leave us? Perhaps the key takeaway is that even if you apply stringent personal security measures, your account credentials can still get caught up in such collections, primarily due to breaches at large companies. This begs the question – how can you find out if your credentials have been compromised? Read on.
Company disclosures
Business may be subject to specific regulatory requirements that oblige them to disclose hacking incidents and unpatched vulnerabilities. In the U.S., for instance, publicly-traded companies need to report “material” cyber-incidents to the U.S. Securities and Exchange Commission (SEC) within 96 hours, or four business days, of their occurrence.
How does this help regular folk? Such transparency may not only help build trust with customers but it also informs them if their accounts or data have been compromised. Companies typically notify users of data breaches via email, but since SEC filings are public, you may learn about such incidents from other sources, possibly even news reports covering them.
Have I been pwned?
Perhaps the simplest way of checking whether some of your data, such as your email address or any of your passwords, has been exposed in a data leak is to visit haveibeenpwned.com. The site features a free tool that can tell you when and where your data popped up.
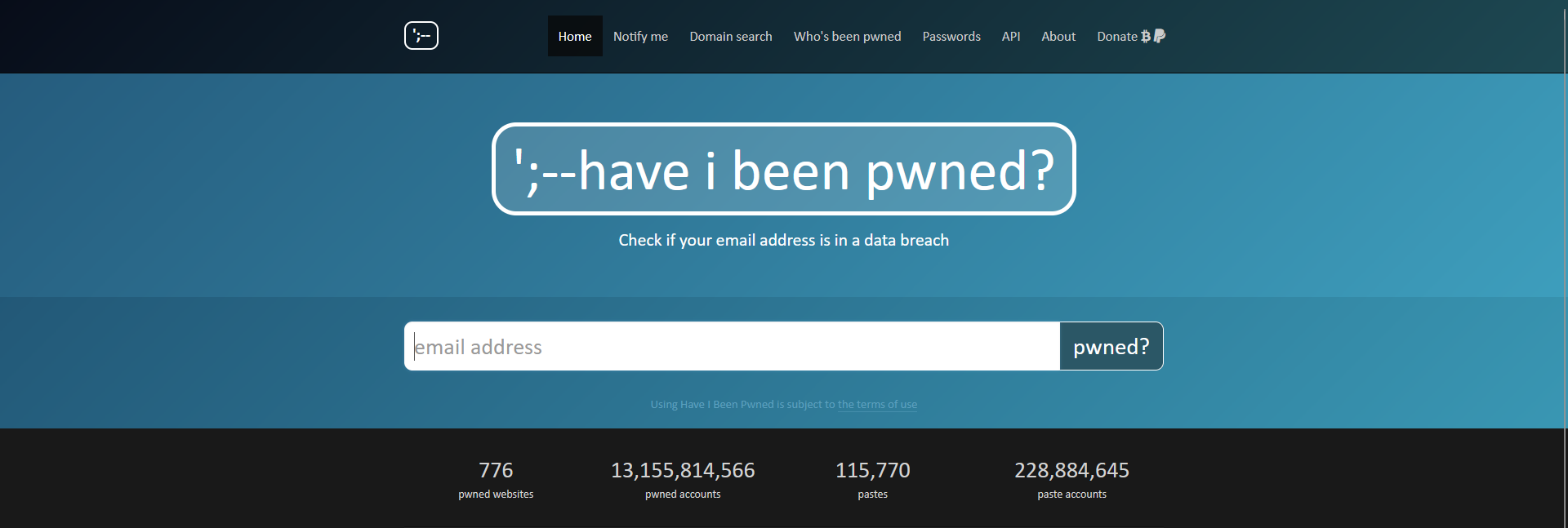
Simply input your email address, click “pwned?” and voila! A message will appear informing you of the security status of your credentials as well as the exact leak they were caught up in. For those who are lucky, the result will be green, signaling no pwnage, and for those less fortunate, the site will turn red, listing in which data leak(s) your credentials appeared.
Web browsers
Some web browsers, including Google Chrome and Firefox, can check if your passwords have been included in any known data leak. Chrome can also recommend stronger passwords via its password manager module or offer other features to enhance your password security.
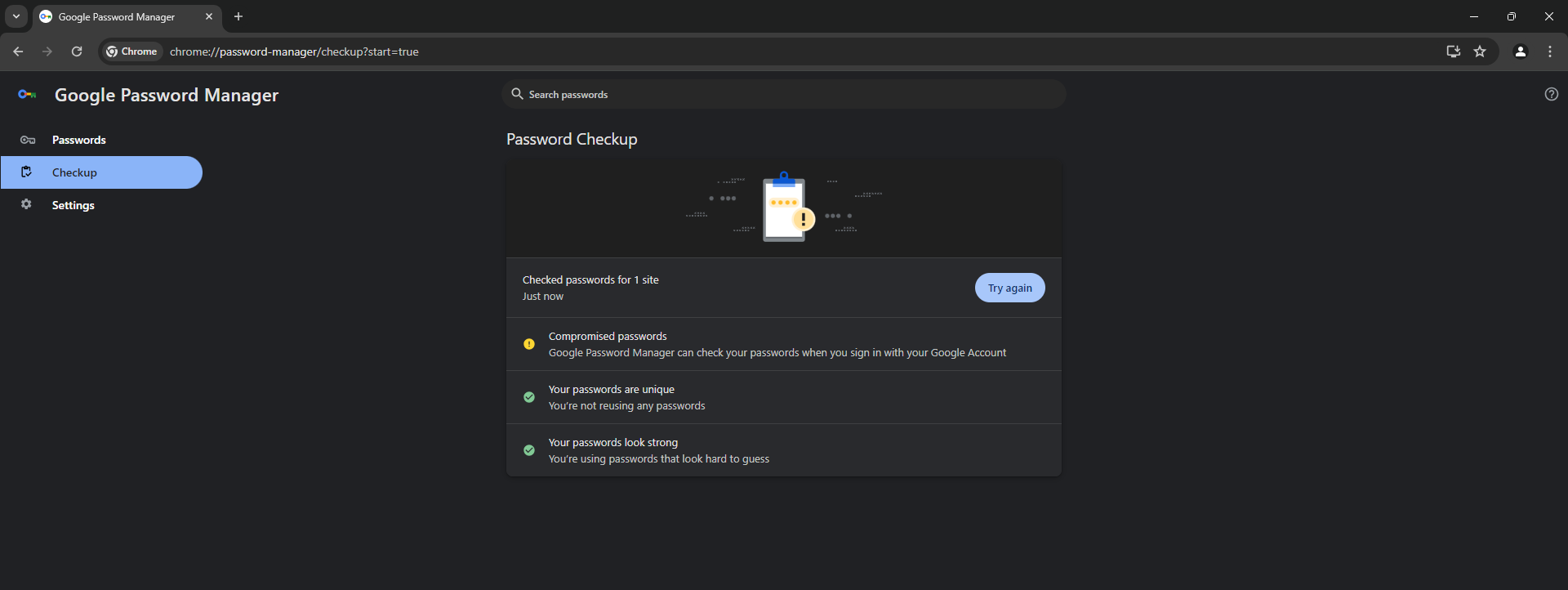
However, you may want to up your game further and use a dedicated password manager that has a proven track record of taking data security seriously, including via robust encryption. These tools are also often bundled with reputable multi-layered security software.
Password managers
Password managers are invaluable when it comes to juggling a large collection of login credentials, as they can not only securely store them, but generate complex and unique passwords for each of your online accounts. It should go without saying, however, that you need to use a strong but memorable master password that holds the keys to your kingdom.
On the other hand, these password vaults aren’t immune to compromise and remain attractive targets for malicious actors, for example as a result of credential-stuffing attacks or attacks exploiting software vulnerabilities. Even so, the benefits – which include built-in leaked password checks and integration with two-factor authentication (2FA) schemes that are available on many online platforms these days – outweigh the risks.
How to prevent (the impact of) credential leaks?
Now, what about preventing leaks in the first place? Can an average internet user protect themselves against credential leaks? If so, how? Indeed, how can you keep your accounts safe?
First of all, and we can’t stress this enough, don’t rely on passwords alone. Instead, make sure your accounts are protected by two forms of identification. To that end, use two-factor authentication (2FA) on every service that enables it, ideally in the form of a dedicated security key for 2FA or an authenticator app such as Microsoft Authenticator or Google Authenticator. This will make it significantly harder for attackers to gain unauthorized access to your accounts – even if they have somehow got their hands on your password(s).
Related reading: Microsoft: 99.9 percent of hacked accounts did not use MFA
As for password security as such, avoid writing your logins down on paper or storing them in a note-taking app. It’s also better to avoid storing your account credentials in web browsers, which usually only store them as simple text files, making them vulnerable to data exfiltration by malware.
Other basic account security tips involve using strong passwords, which make it harder for crooks to commit brute-force attacks. Stay away from simple and short passwords, such as a word and a number. When in doubt, use this ESET tool to generate your passwords, or have it check the strength of your own passwords.
Related reading: How often should you change your passwords?
It’s also good practice to use passphrases, which can be safer as well as easier to remember. Instead of random letter and symbol combinations, they comprise a series of words that are sprinkled by capitals and possibly special characters.
Likewise, use a different password for each of your accounts to prevent attacks such as credential stuffing, which takes advantage of people’s penchant for reusing the same credentials across multiple online services.
A newer approach to authentication relies on passwordless logins, such as passkeys, and there are also other login methods like security tokens, one-time codes or biometrics to verify account ownership across multiple devices and systems.
Company-side prevention
Companies need to invest in security solutions, such as detection and response software, that can prevent breaches and security incidents. Additionally, organizations need to proactively shrink their attack surface and react as soon as something suspicious is detected. Vulnerability management is also crucial, as staying on top of known software loopholes and patching them in a timely manner helps prevent exploitation by cybercriminals.
Meanwhile, the ever-present human factor can also trigger a compromise, for example after an employee opens a suspicious email attachment or clicks a link. This is why the importance of cybersecurity awareness training and endpoint/mail security cannot be understated.
Related reading: Strengthening the weakest link: top 3 security awareness topics for your employees
Any company that seriously tackles data security should also consider a data loss prevention (DLP) solution and implement a robust backup policy.
Additionally, handling large volumes of client and employee data requires stringent encryption practices. Local encryption of credentials can safeguard such sensitive data, making it difficult for attackers to exploit stolen information without access to the corresponding encryption keys.
All in all, there is no one-size-fits-all solution, and every company needs to tailor its data security strategy to its specific needs and adapt to the evolving threat landscape. Nevertheless, a combination of cybersecurity best practices will go a long way towards preventing data breaches and leaks.
Source link
lol
How To Password leaks are increasingly common and figuring out whether the keys to your own kingdom have been exposed might be tricky – unless you know where to look 03 Jun 2024 • , 6 min. read Recently, I came across a report detailing “the mother of all breaches” – or to be more…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
