New Warmcookie Windows backdoor pushed via fake job offers
by nlqip

A never-before-seen Windows malware named ‘Warmcookie’ is distributed through fake job offer phishing campaigns to breach corporate networks.
According to Elastic Security Labs, which discovered the new threat, Warmcookie is capable of extensive machine fingerprinting, screenshot capturing, and the deployment of additional payloads.
The campaign is currently underway, and the threat actors create new domains weekly to support their malicious operations, using compromised infrastructure to send phishing emails.
Fake job offers push malware
The phishing campaign utilizes fake job and recruitment offers sent via emails with attention-grabbing subjects. They target individuals with touches of personalization, using their names and those of their current employers.
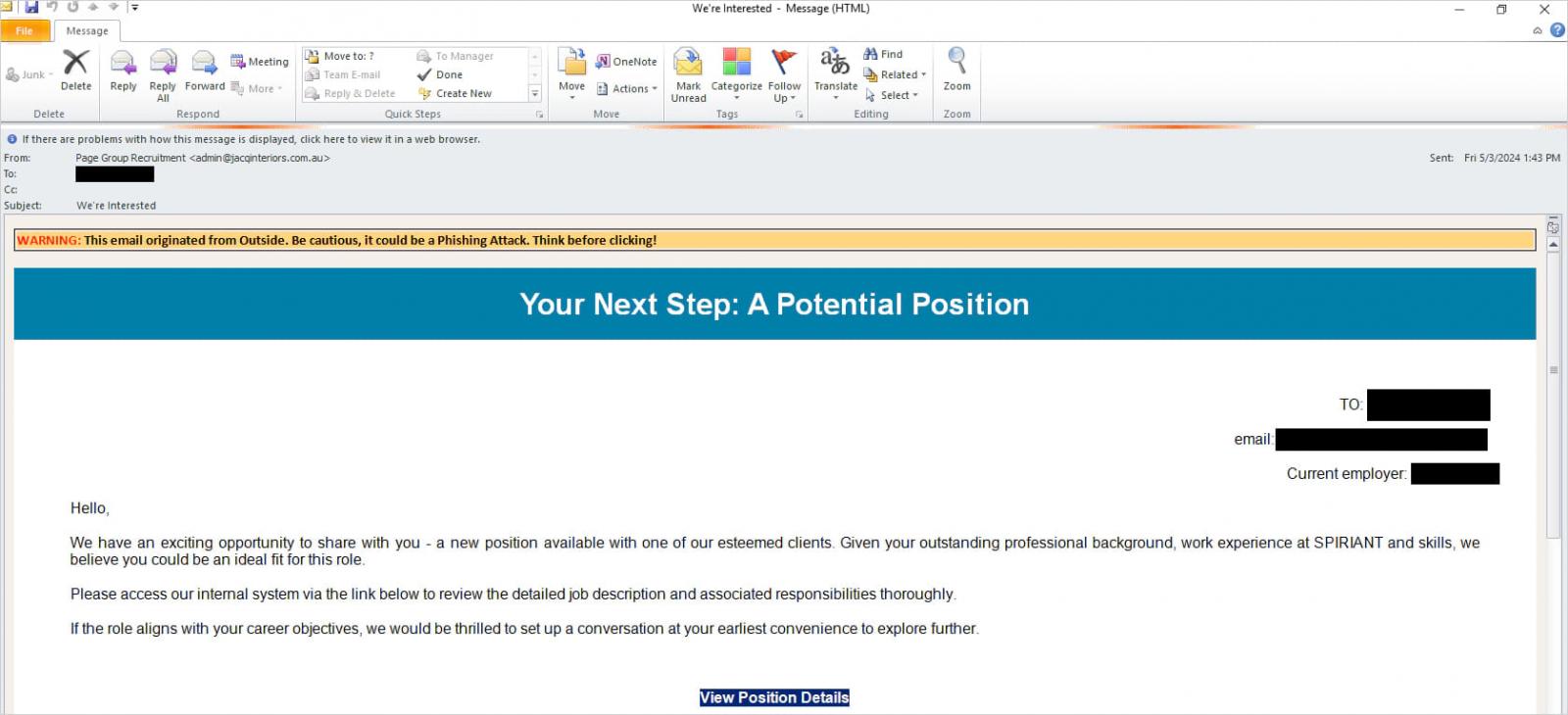
Source: Elastic
The emails contain a link that claims to be for an internal recruitment platform where the job description can be viewed but redirects the user to landing pages mimicking legitimate platforms.
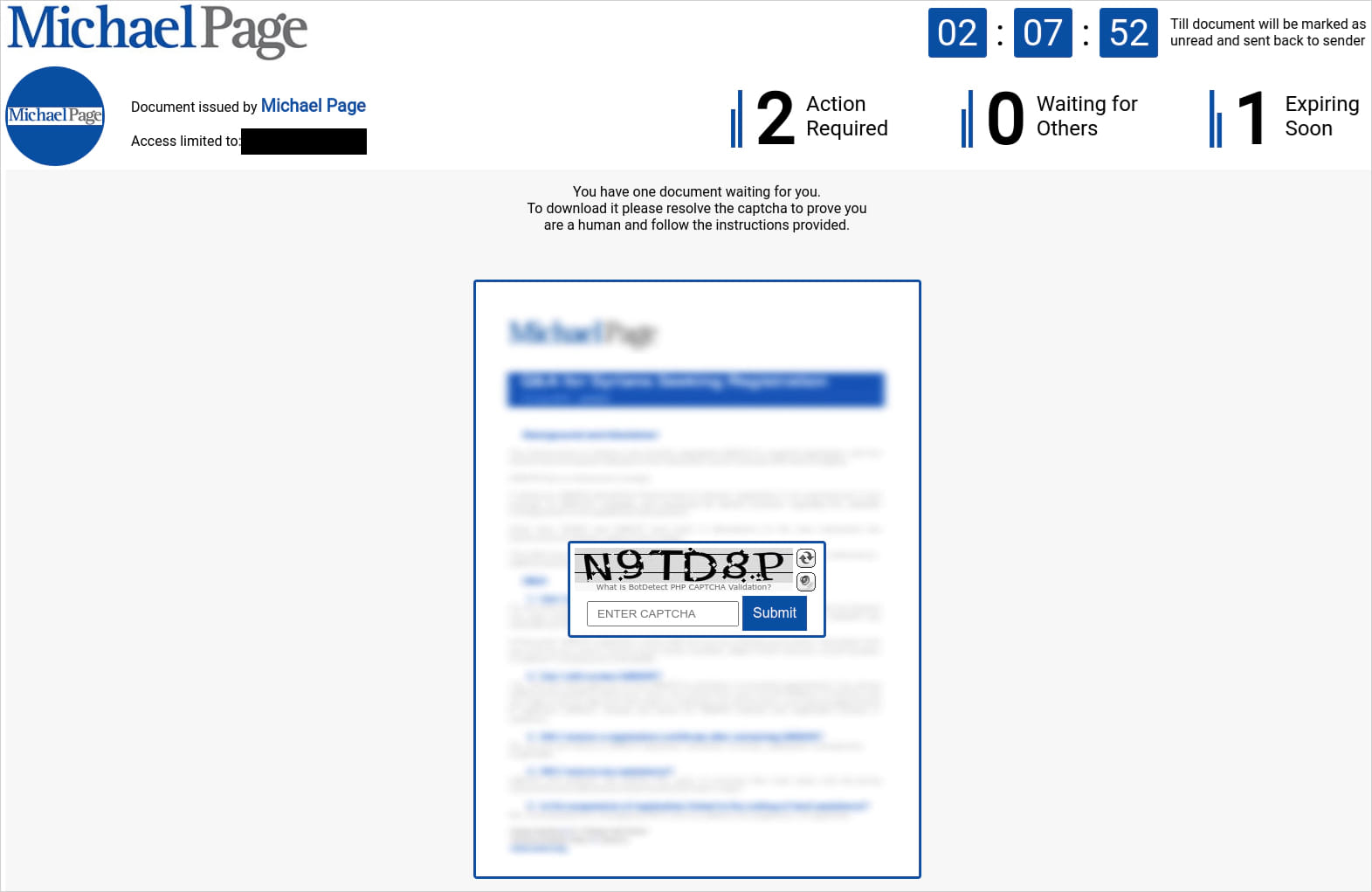
Source: Elastic
To add legitimacy, those fake pages prompt the victim to solve a CAPTCHA before they download a heavily obfuscated JavaScript file named similar to ‘Update_23_04_2024_5689382’.
When executed, the JS script executes a PowerShell script that uses the Background Intelligent Transfer Service (BITS) to download the Warmcookie DLL file from a specified URL and execute it via rundll32.exe.
The Warmcookie payload is copied to C:ProgramDataRtlUpdRtlUpd.dll, and upon first execution, it creates a scheduled task named ‘RtlUpd’ that runs every 10 minutes.
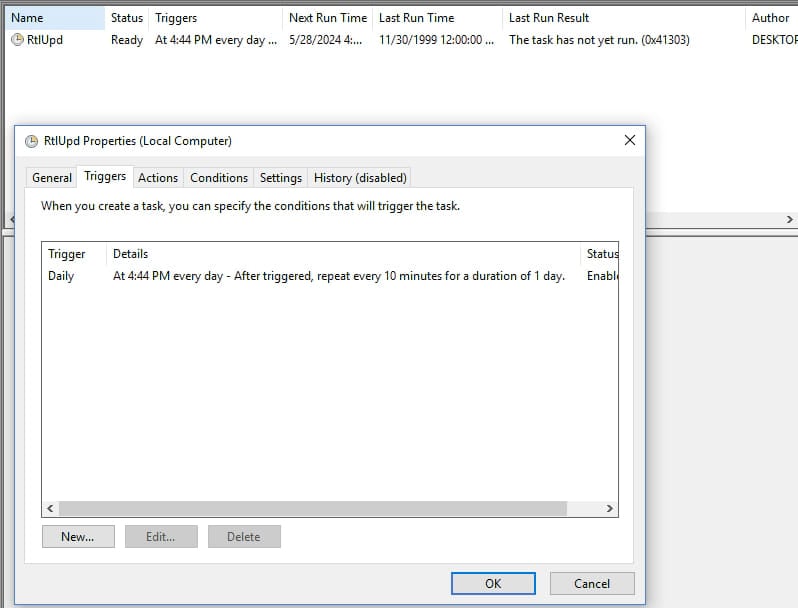
Source: Elastic
In the final setup phase, Warmcookie establishes communication with its command and control (C2) server and begins fingerprinting the victim’s machine.
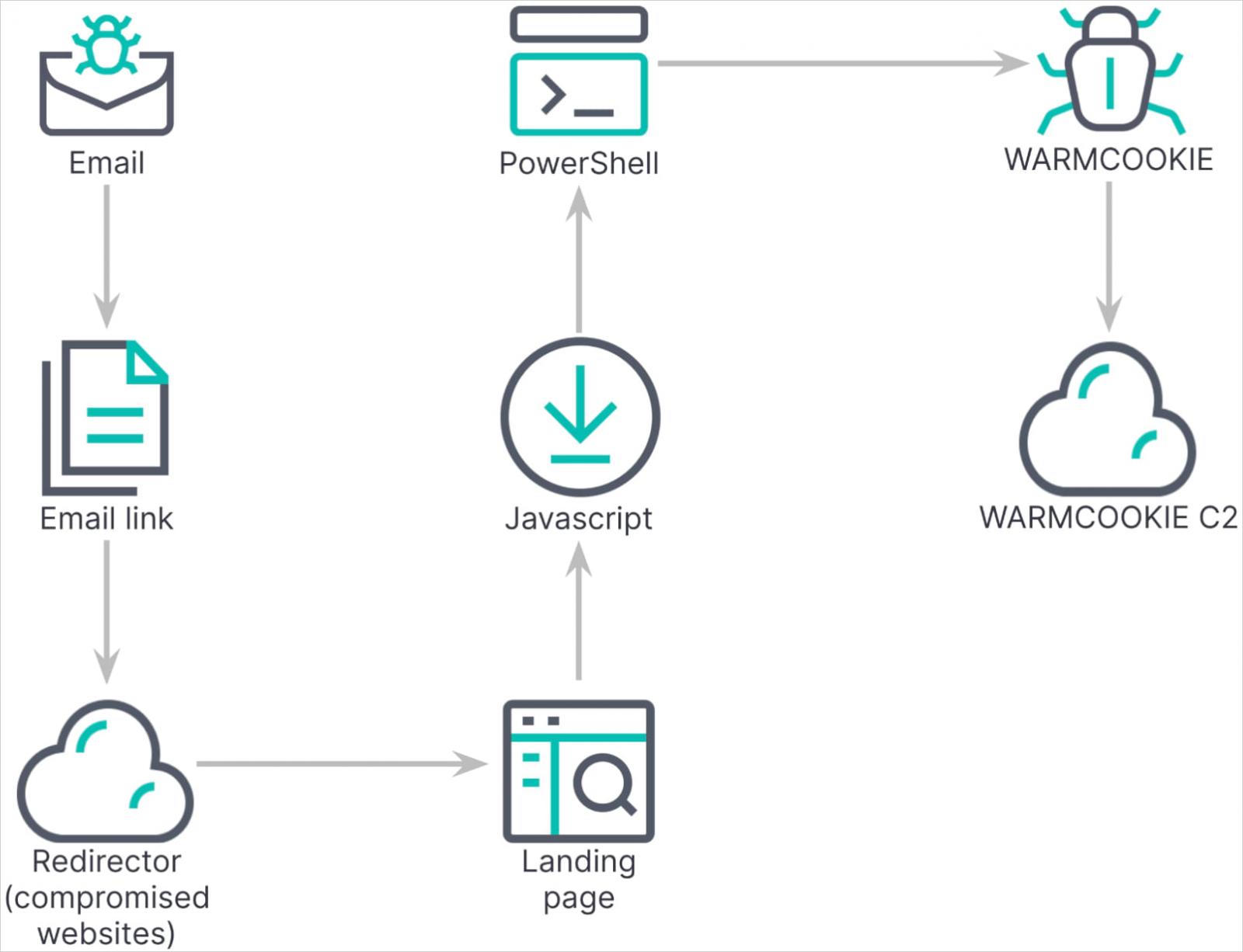
Source: Elastic
Warmcookie capabilities
Warmcookie is a backdoor malware with various capabilities designed to infiltrate, persist, and gather intelligence from victim systems.
In the first stage of its operation, it collects key information about the infected host, including volume serial number, DNS domain, computer name, and username, and then encrypts and sends the data to the C2 through the HTTP cookie parameter.
Warmcookie’s main capabilities are:
- Retrieve victim information such as IP address and CPU details
- Capture screenshots using Windows native tools
- Enumerate installed programs via the registry key
- Execute arbitrary commands using ‘cmd.exe’ and send output to the C2
- Drop files on specified directories/paths
- Read the contents of specified files and send content to C2
Source: Elastic
All received commands are processed via an integrity check using CRC32 checksums to ensure they haven’t been tampered with.
Also, the malware won’t run if the number of CPU processors and physical/virtual memory values are below certain thresholds to evade analysis environments.
Elastic’s analysts comment that despite Warmcookie being a new backdoor with plenty of room for improvement, it is already entirely capable of inflicting significant damage to its targets, especially given its capability to introduce additional payloads.
Source link
lol
Image: Midjourney A never-before-seen Windows malware named ‘Warmcookie’ is distributed through fake job offer phishing campaigns to breach corporate networks. According to Elastic Security Labs, which discovered the new threat, Warmcookie is capable of extensive machine fingerprinting, screenshot capturing, and the deployment of additional payloads. The campaign is currently underway, and the threat actors create new…
Recent Posts
- Telegram for Android hit by a zero-day exploit – Week in security with Tony Anscombe
- French Authorities Launch Operation to Remove PlugX Malware from Infected Systems
- Malicious PyPI Package Targets macOS to Steal Google Cloud Credentials
- Secure Boot no more? Leaked key, faulty practices put 900 PC/server models in jeopardy
- Crooks Bypassed Google’s Email Verification to Create Workspace Accounts, Access 3rd-Party Services – Krebs on Security
