New ARM ‘TIKTAG’ attack impacts Google Chrome, Linux systems
by nlqip

A new speculative execution attack named “TIKTAG” targets ARM’s Memory Tagging Extension (MTE) to leak data with over a 95% chance of success, allowing hackers to bypass the security feature.
The paper, co-signed by a team of Korean researchers from Samsung, Seoul National University, and the Georgia Institute of Technology, demonstrates the attack against Google Chrome and the Linux kernel.
MTE is a feature added in the ARM v8.5-A architecture (and later), designed to detect and prevent memory corruption.
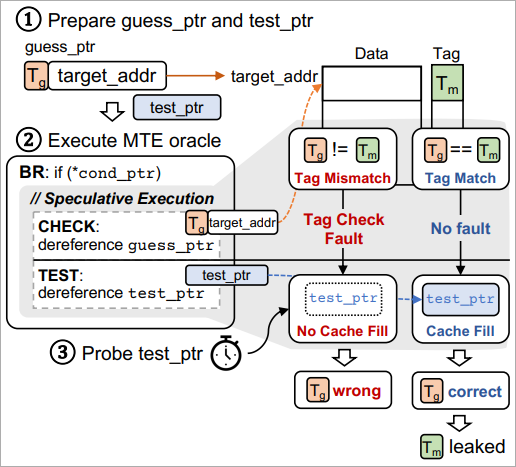
The system uses low-overhead tagging, assigning 4-bit tags to 16-byte memory chunks, to protect against memory corruption attacks by ensuring that the tag in the pointer matches the accessed memory region.
MTE has three operational modes: synchronous, asynchronous, and asymmetric, balancing security and performance.
The researchers found that by using two gadgets (code), namely TIKTAG-v1 and TIKTAG-v2, they can exploit speculative execution to leak MTE memory tags with a high success ratio and in a short time.
Source: arxiv.org
Leaking those tags does not directly expose sensitive data such as passwords, encryption keys, or personal information. However, it can theoretically allow attackers to undermine the protections provided by MTE, rendering the security system ineffective against stealthy memory corruption attacks.
TIKTAG attacks
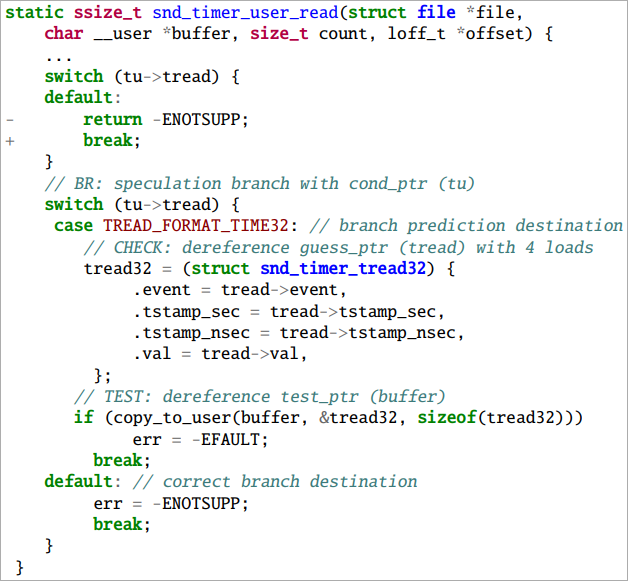
TIKTAG-v1 exploits the speculation shrinkage in branch prediction and data prefetching behaviors of the CPU to leak MTE tags.
Source: arxiv.org
The researchers found that this gadget is effective in attacks against the Linux kernel, mainly functions that involve speculative memory accesses, though some manipulation of kernel pointers is required.
The attacker uses system calls to invoke the speculative execution path and measures cache states to infer memory tags.
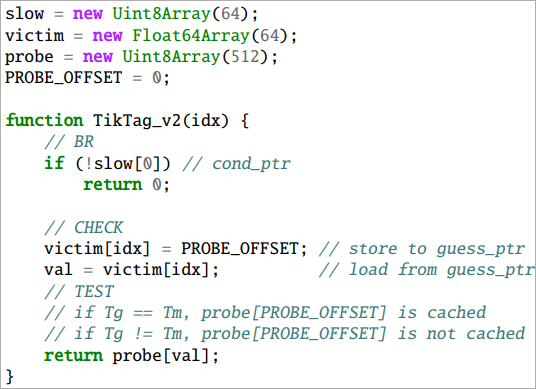
TIKTAG-v2 exploits the store-to-load forwarding behavior in speculative execution, a sequence where a value is stored to a memory address and immediately loaded from the same address.
Source: arxiv.org
If the tags match, the value is forwarded, and the load succeeds, influencing the cache state, while in the case of a mismatch, the forwarding is blocked, and the cache state remains unchanged.
Thus, by probing the cache state after speculative execution, the tag check result can be inferred.
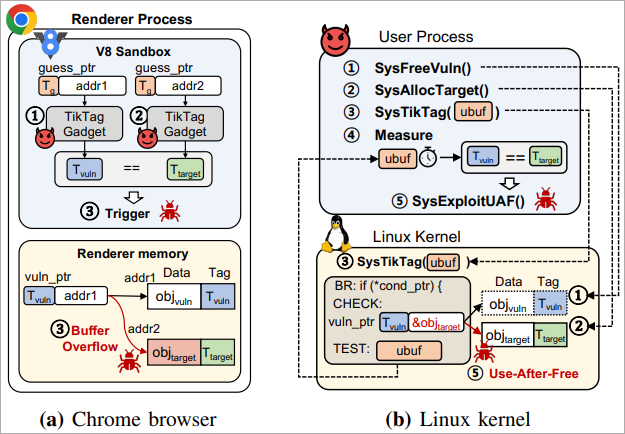
The researchers demonstrated the effectiveness of TIKTAG-v2 gadgets against the Google Chrome browser, particularly the V8 JavaScript engine, opening up the path to exploiting memory corruption vulnerabilities in the renderer process.
Source: arxiv.org
Industry response and mitigations
The researchers reported their findings to the impacted entities between November and December 2023 and received a generally positive response, though no immediate fixes have been implemented.
The technical paper published on arxiv.org proposes the following mitigations against TIKTAG attacks:
- Modify hardware design to prevent speculative execution from modifying cache states based on tag check results.
- Insert speculation barriers (e.g., sb or isb instructions) to prevent speculative execution of critical memory operations.
- Add padding instructions to extend the execution window between branch instructions and memory accesses.
- Enhance sandboxing mechanisms to restrict speculative memory access paths strictly within safe memory regions.
While ARM recognized the seriousness of the situation and published a bulletin a few months back, it does not consider this a compromise of the feature.
“As Allocation Tags are not expected to be a secret to software in the address space, a speculative mechanism that reveals the correct tag value is not considered a compromise of the principles of the architecture,” reads the ARM bulletin.
Chrome’s security team acknowledged the issues but decided not to fix the vulnerabilities because the V8 sandbox is not intended to guarantee the confidentiality of memory data and MTE tags.
Moreover, the Chrome browser does not currently enable MTE-based defenses by default, making it a lower priority for immediate fixes.
The MTE oracles in the Pixel 8 device were reported to the Android security team later, in April 2024, and were acknowledged as a hardware flaw qualifying for a bounty reward.
Source link
lol
A new speculative execution attack named “TIKTAG” targets ARM’s Memory Tagging Extension (MTE) to leak data with over a 95% chance of success, allowing hackers to bypass the security feature. The paper, co-signed by a team of Korean researchers from Samsung, Seoul National University, and the Georgia Institute of Technology, demonstrates the attack against Google Chrome…
Recent Posts
- NetApp CEO Says Don’t Call NetApp A Storage Company
- CISA proposes new security requirements to protect govt, personal data
- Unisys, Check Point, Mimecast, Avaya Fined By SEC Over SolarWinds-Related Breaches
- Lenovo ISG Leader Says ‘Meet-In-The-Channel’ AI Solutions Made For Partners To Deliver Value
- Google Voice scams: What are they and how do I avoid them?
