Month: June 2024
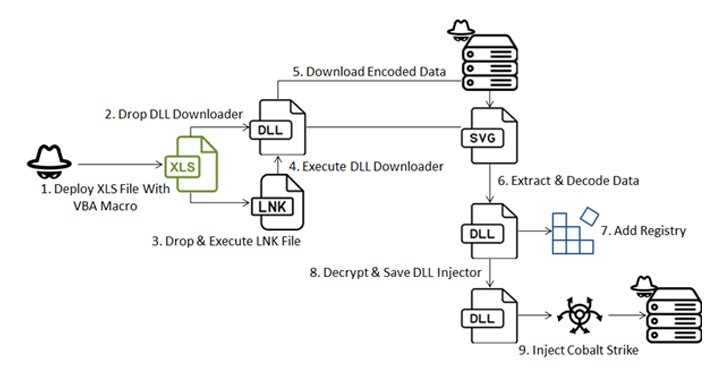
Jun 04, 2024NewsroomCyber Attack / Malware A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per Fortinet FortiGuard Labs, involves a Microsoft Excel file that carries an embedded VBA macro to initiate the infection,…
Read MoreJun 04, 2024The Hacker NewsBrowser Security / Enterprise Security The landscape of browser security has undergone significant changes over the past decade. While Browser Isolation was once considered the gold standard for protecting against browser exploits and malware downloads, it has become increasingly inadequate and insecure in today’s SaaS-centric world. The limitations of Browser Isolation,…
Read MoreWhile public pricing for CPUs has been standard in the data center industry, it’s been the opposite case for GPUs and other kinds of accelerator chips. An Intel exec explains to CRN why the company is changing its stance with the upcoming Gaudi 3 AI chips. Intel said it’s upending a norm of secrecy in…
Read MoreFix includes updating to the latest version The vulnerability affects versions 5.2, 7.19.0, 7.20.0, 8.0.0, 8.1.0, 8.2.0, 8.3.0, 8.4.0, 8.5.0, 8.6.0, 8.8.0, 8.7.1, 8.9.0 of Confluence Data Center as well as Atlassian Server. Fixes for the flawed software are included in the versions 8.9.1, 8.5.9, and 7.19.22, patching all the affected versions. “Atlassian recommends that Confluence Server…
Read MoreCVE-2024-4358, CVE-2024-1800: Exploit Code Available for Critical Exploit Chain in Progress Telerik Report Server
by nlqip
Researchers have released an exploit chain to achieve remote code execution on unpatched instances of Progress Telerik Report Server. Immediate patching is recommended. Background On May 31, security researcher Sina Kheirkhah of the Summoning Team posted on X (formerly known as Twitter) the discovery of an exploit chain involving two vulnerabilities in Progress Telerik Report…
Read MoreBreaking a Password Manager Interesting story of breaking the security of the RoboForm password manager in order to recover a cryptocurrency wallet password. Grand and Bruno spent months reverse engineering the version of the RoboForm program that they thought Michael had used in 2013 and found that the pseudo-random number generator used to generate passwords…
Read MoreJun 04, 2024NewsroomCloud Security / Data Protection Cloud computing and analytics company Snowflake said a “limited number” of its customers have been singled out as part of a targeted campaign. “We have not identified evidence suggesting this activity was caused by a vulnerability, misconfiguration, or breach of Snowflake’s platform,” the company said in a joint…
Read MorePenetration testing is a cornerstone of any mature security program and is a mature and well understood practice supported by robust methodologies, tools, and frameworks. The tactical goals of these engagements typically revolve around identification and exploitation of vulnerabilities in technology, processes, and people to gain initial, elevated, and administrative access to the target environment.…
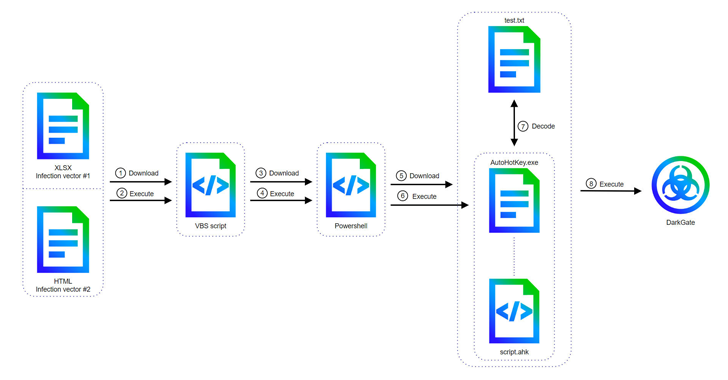
Read MoreJun 04, 2024NewsroomVulnerability / Threat Intelligence Cyber attacks involving the DarkGate malware-as-a-service (MaaS) operation have shifted away from AutoIt scripts to an AutoHotkey mechanism to deliver the last stages, underscoring continued efforts on the part of the threat actors to continuously stay ahead of the detection curve. The updates have been observed in version 6…
Read MoreHow To Password leaks are increasingly common and figuring out whether the keys to your own kingdom have been exposed might be tricky – unless you know where to look 03 Jun 2024 • , 6 min. read Recently, I came across a report detailing “the mother of all breaches” – or to be more…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA