Author: nlqip
Breaking a Password Manager Interesting story of breaking the security of the RoboForm password manager in order to recover a cryptocurrency wallet password. Grand and Bruno spent months reverse engineering the version of the RoboForm program that they thought Michael had used in 2013 and found that the pseudo-random number generator used to generate passwords…
Read MoreJun 04, 2024NewsroomCloud Security / Data Protection Cloud computing and analytics company Snowflake said a “limited number” of its customers have been singled out as part of a targeted campaign. “We have not identified evidence suggesting this activity was caused by a vulnerability, misconfiguration, or breach of Snowflake’s platform,” the company said in a joint…
Read MorePenetration testing is a cornerstone of any mature security program and is a mature and well understood practice supported by robust methodologies, tools, and frameworks. The tactical goals of these engagements typically revolve around identification and exploitation of vulnerabilities in technology, processes, and people to gain initial, elevated, and administrative access to the target environment.…
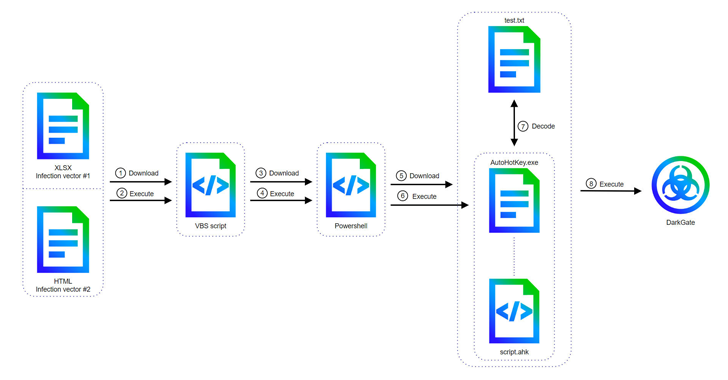
Read MoreJun 04, 2024NewsroomVulnerability / Threat Intelligence Cyber attacks involving the DarkGate malware-as-a-service (MaaS) operation have shifted away from AutoIt scripts to an AutoHotkey mechanism to deliver the last stages, underscoring continued efforts on the part of the threat actors to continuously stay ahead of the detection curve. The updates have been observed in version 6…
Read MoreHow To Password leaks are increasingly common and figuring out whether the keys to your own kingdom have been exposed might be tricky – unless you know where to look 03 Jun 2024 • , 6 min. read Recently, I came across a report detailing “the mother of all breaches” – or to be more…
Read MoreRepresentative attack vectors to simulate a wide range of attacks relevant to your company. Realistic attack scenarios that are similar to what attackers are actually using, using frameworks such as MITRE ATT&CK. Customizable scenarios to test unique aspects of your infrastructure. Automated testing so that the simulations can run regularly and efficiently without impacting operations…
Read MoreIs CISM worth it? CISM salary CISM certification involves a number of steps, so the obvious question arises: Is it worth it? If you’re interested in a management position — and the higher salaries such positions command — earning a CISM certification is a great way to signal your expertise, as well as your seriousness…
Read MoreJun 04, 2024NewsroomNetwork Security / Cryptocurrency The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Oracle WebLogic Server to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2017-3506 (CVSS score: 7.4), the issue concerns an operating system (OS) command injection vulnerability that could…
Read More‘CISOs that have been struggling with security and compliance tell us all the time that this is exactly what they need,’ says Aqueduct Technologies CTO Shane O’Brien. ‘This is a compliance game changer for customers.’ Aqueduct Technologies Chief Technology Officer Shane O’Brien is no longer surprised by the look of amazement he gets from CISOs…
Read MoreMicrosoft will cut as many as 1,500 in Azure for Operators and Mission Engineering, according to Business Insider. Microsoft is reportedly laying off hundreds of employees in Azure and its mixed reality businesses. Business Insider reported Monday that Microsoft will cut as many as 1,500 in Azure for Operators and Mission Engineering. This is part…
Read MoreRecent Posts
- Lumen Technologies CEO: ‘We’re Building The Backbone For The AI Economy’
- 9 Steps to Get CTEM on Your 2025 Budgetary Radar
- INTERPOL Disrupts Over 22,000 Malicious Servers in Global Crackdown on Cybercrime
- Singtel Hack Highlights Rising Threat of Chinese Cyber Attacks on Global Telecoms
- South Korea Fines Meta $15.67M for Illegally Sharing Sensitive User Data with Advertisers