Category: Viral
There’s a huge untapped market for MSPs in helping small organizations adopt secure access service edge, which offers lower costs, better security and a simple deployment. For many SMB and midmarket customers, the only thing holding them back from shifting to newer cloud-delivered approaches for network security at this point is awareness of the option—and…
Read MoreNetwork Security Devices Are The Front Door To An IT Environment, But Are They Under Lock And Key?
by nlqip
As the industry has gotten better at locking down endpoint devices such as laptops, threat actors are finding new ways to infiltrate an organization’s systems—and they’re seeing more and more success. From the widespread compromise of Ivanti VPNs to a string of cyberattacks involving vulnerabilities in on-premises firewalls, this year has seen threat actors increasingly…
Read MoreThe advisory recommends that Snowflake customers perform hunting activities for malicious activity in their systems. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning about the recent threat actor campaign targeting users of Snowflake and urging customers to proactively look for malicious activity. In the advisory, CISA pointed to a post from Snowflake on…
Read More‘[AI is] changing the way businesses communicate with each other. It’s changing the way they leverage technology. And at Cisco, we believe we have a very significant role to play here in really being the trusted partner to help our customers navigate this new era of AI,’ says Mark Patterson, Cisco’s executive vice president and…
Read MoreJun 04, 2024NewsroomServer Security / Vulnerability Progress Software has rolled out updates to address a critical security flaw impacting the Telerik Report Server that could be potentially exploited by a remote attacker to bypass authentication and create rogue administrator users. The issue, tracked as CVE-2024-4358, carries a CVSS score of 9.8 out of a maximum…
Read MoreHere are the five biggest new integrated product launches from SAP and Google Cloud unveiled at SAP Sapphire 2024 Tuesday that all partners and customers need to know about. SAP and Google Cloud launched a slew of new innovations together at SAP Sapphire 2024 Tuesday in Orlando, Fla., including a new AI-powered offering to enable…
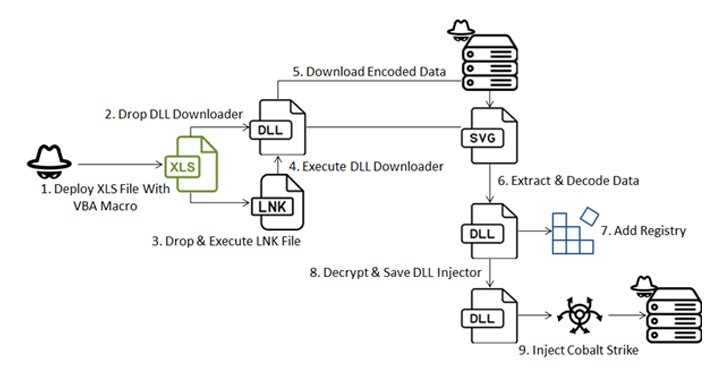
Read MoreJun 04, 2024NewsroomCyber Attack / Malware A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per Fortinet FortiGuard Labs, involves a Microsoft Excel file that carries an embedded VBA macro to initiate the infection,…
Read MoreWhile public pricing for CPUs has been standard in the data center industry, it’s been the opposite case for GPUs and other kinds of accelerator chips. An Intel exec explains to CRN why the company is changing its stance with the upcoming Gaudi 3 AI chips. Intel said it’s upending a norm of secrecy in…
Read MoreJun 04, 2024NewsroomCloud Security / Data Protection Cloud computing and analytics company Snowflake said a “limited number” of its customers have been singled out as part of a targeted campaign. “We have not identified evidence suggesting this activity was caused by a vulnerability, misconfiguration, or breach of Snowflake’s platform,” the company said in a joint…
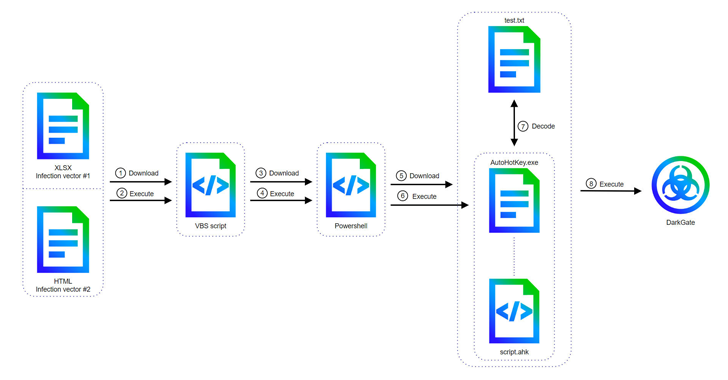
Read MoreJun 04, 2024NewsroomVulnerability / Threat Intelligence Cyber attacks involving the DarkGate malware-as-a-service (MaaS) operation have shifted away from AutoIt scripts to an AutoHotkey mechanism to deliver the last stages, underscoring continued efforts on the part of the threat actors to continuously stay ahead of the detection curve. The updates have been observed in version 6…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption