Jun 11, 2024NewsroomCloud Computing / Artificial Intelligence Apple has announced the launch of a “groundbreaking cloud intelligence system” called Private Cloud Compute (PCC) that’s designed for processing artificial intelligence (AI) tasks in a privacy-preserving manner in the cloud. The tech giant described PCC as the “most advanced security architecture ever deployed for cloud AI compute…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. From humble beginnings as a niche hobby relegated to small gaming cafes and basements, eSports has grown into a huge affair where gamers…
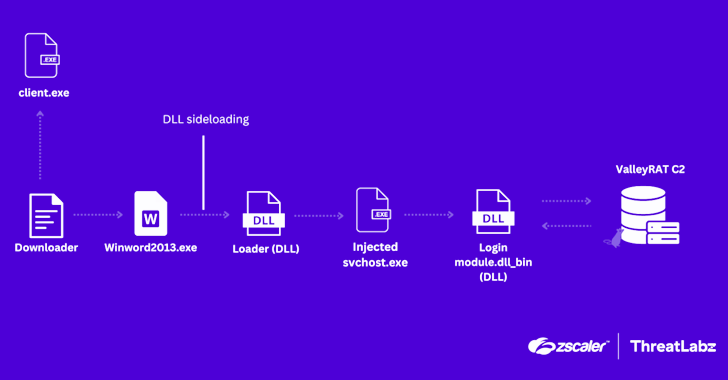
Read MoreJun 11, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have uncovered an updated version of malware called ValleyRAT that’s being distributed as part of a new campaign. “In the latest version, ValleyRAT introduced new commands, such as capturing screenshots, process filtering, forced shutdown, and clearing Windows event logs,” Zscaler ThreatLabz researchers Muhammed Irfan V A and…
Read MoreJun 11, 2024NewsroomMobile Security / Technology Arm is warning of a security vulnerability impacting Mali GPU Kernel Driver that it said has been actively exploited in the wild. Tracked as CVE-2024-4610, the use-after-free issue impacts the following products – “A local non-privileged user can make improper GPU memory processing operations to gain access to already…
Read MoreJun 11, 2024NewsroomData Theft / Cloud Security As many as 165 customers of Snowflake are said to have had their information potentially exposed as part of an ongoing campaign designed to facilitate data theft and extortion, indicating the operation has broader implications than previously thought. Google-owned Mandiant, which is assisting the cloud data warehousing platform…
Read MoreDigital Security The award is an excellent opportunity for us to thank our readers and to recognize the depth of talent of ESET’s security researchers and writers 10 Jun 2024 • , 2 min. read Drumroll, please! The winners of the 2024 European Cybersecurity Blogger Awards have been chosen, and we couldn’t be prouder –…
Read MoreA failure to consider cybersecurity when it comes to engaging in an M&A deal, as Winzer put it, is like driving blind without any mirrors. “You can be very easily attacked and become prey to cyber attackers, and if that were to happen what’s at stake is business operations, being able to run the company…
Read MoreInformation security analyst/administrator Information assurance security officer Information security manager/specialist Information systems security engineer/manager Information security professionals/officers Information security/IT auditors Risk/threat/vulnerability analyst System administrators Network administrators and engineers This is, of course, over and above jobs that actually have “ethical hacker” or “penetration testing” or the like in their title, which are more glamorous but…
Read MoreArm has issued a security bulletin warning of a memory-related vulnerability in Bifrost and Valhall GPU kernel drivers that is being exploited in the wild. The security issue is tracked as CVE-2024-4610 and is a use-after-free vulnerability (UAF) that impacts all versions of Bifrost and Valhall drivers from r34p0 through r40p0. UAF flaws occur when a program…
Read MoreThreat actors impersonate GitHub’s security and recruitment teams in phishing attacks to hijack repositories using malicious OAuth apps in an ongoing extortion campaign wiping compromised repos. Since at least February, dozens of developers targeted in this campaign have received similar fake job offers or security alert emails from “notifications@github.com” after being tagged in spam comments…
Read MoreRecent Posts
- AWS CEO Suggests Workers Leave If They’re Not Returning To The Office: Report
- Microsoft warns it lost some customer’s security logs for a month
- Cohesity CEO On AI, Data Protection, Data Insights And Impacts On The Channel
- Fake Google Meet conference errors push infostealing malware
- Lenovo Tech World: 5 Biggest Product, Software Launches